The word on the street is not “If I get hacked” but “when I will get hacked” and securing your infrastructure starts from your end users and devices and hardening those devices that the users use every day has never been so important. Security Baseline policy for Windows 10 and later. This is one of the recommended policies that just needs to be created at a minimum level and the latest settings template will be assigned to the devices. I would say the effort to configure this policy is just less than 5% of what needs to be enabled to give your device that “acceptable” security configuration. This is somewhat similar to other famous security frameworks as the recommendations have been created by the Microsoft Security teams as a way to close the gaps as well as to enhance the end-user device’s security posture.
- Intune Enrolled and MDE Onboarded Requirement
- Windows Version Requirement
- Licensing Requirement
- Where to Find the Baselines
- Policy Sync Times
- Group Policy Over Intune Polcies
- Piloting Before Rolling Out
- User Noise and Fine-Tuning
- Duplicating Policies
- Keeping it Up to Date – Changing Baseline Versions
- Compare Policies
- Changing Baseline Version
- Conflicting Settings With Other Policies
- Advanced Settings Available in Other Security Polices
- Removing Baseline And Settings Tattooing Issue
- Reporting
- Monitor Assignment Failures and Dig Into the Settings and Devices With the Issue
- Error Handling
- Wrapping Up
UPDATE!
Security Baseline for Windows 10 and later Version 23H2 is now available!
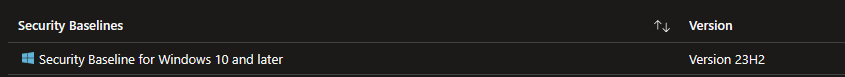
🔗 Learn Link: https://learn.microsoft.com/en-us/mem/intune/protect/security-baseline-settings-mdm-all?pivots=mdm-23h2
The good thing about the baseline is, that it covers pretty much all the critical areas of the device regarding security, and you can build your advanced policies on top of this. This article includes my experience and texts from Microsoft Docs which I found useful.
At a glance, Security Baseline will,
Stop SMBv1, Enable Windows Defender Firewall, Enable Defender AV settings, Control LM Compatibility settings (LM, NTLM, NTLMv2), Disables Autoplay, Manage Smart Screen and the list goes on
Intune Enrolled and MDE Onboarded Requirement
The device needs to be enrolled into Intune and onboarded into Defender for Endpoint in order to use the full feature set of this as this has both Intune and MDE setting enforcements. Device assignment will be done via Entra ID groups.
Windows Version Requirement
- Windows 10 version 1809 and later
- Windows 11
Licensing Requirement
- Microsoft Defender for Endpoint P1 or P2 – to cover the Defender-related settings
- An Intune license for Device Management settings
Where to Find the Baselines
Intune Portal > Endpoint Security > Security baselines > Security Baseline for Windows 10 and later

Policy Sync Times
- 24 hours to fully apply the policy to the workstation
- Any changes to the policy will take 6 hours to appear
Group Policy Over Intune Polcies
Worth noting and a reminder to check your GPOs. Chances are some policy settings may have already been implemented via GPO(s). If that’s the case, this is a good time to move that function to Intune. Also, you may need to consider the MDM Wins Over GPO configuration policy.
You can use the Setting Catalog to create a policy and assign it to the same device group.


Piloting Before Rolling Out
It is highly advisable to pilot the Baseline Policy in few computers as the user experience can be tough if they start getting disruptions. Plan your comms so the users know there is a change coming that protects their workstations better.
User Noise and Fine-Tuning
This comes to the User noise and fine-tuning. It is important the security team evaluate and review the settings and identify user impacts if there are any. I’ll give you an example.
Attack Surface Reduction (ASR) Rules under the Microsoft Defender section. When enabling ASR Rule policies, Microsoft advises enabling them in Audit mode first at least for 30 days and reviewing the reports to see each rule’s impact on user computers. The rules can be quite stringent to set to Block mode at once. However, enabling the Security Baseline Policy will set the ASR rules to Block mode as that is the template Microsoft has created. This is contradicting but be mindful when enabling the baseline as it can make user noise. No finance user would like their Excel Macros to get blocked suddenly. It’s a process.
Likewise, there are few settings that helpdesk might get complaints on. So again, review the policy settings, fine tune if required.
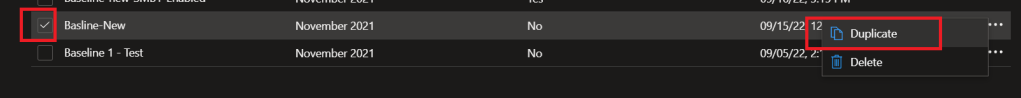
Duplicating Policies
You can easily duplicate a policy and create a new one. The duplicated policy will not get assigned to any device group until you add a group to it.
This method can be handy when you need to change a subset of settings and apply to a pilot set of devices and if all good, then discard it and change the original policy’s settings.
Keeping it Up to Date – Changing Baseline Versions
To keep up with the current Security trends Microsoft keep on updating the Baselines and introducing new settings to it. As a result, the versions of the Baseline get changed. If and when there are version changes, you will see an exclamation mark in front of the policy – meaning its outdated. In that case you need to update it. If you check the Official Microsoft Doc, you can see the current Baseline version in use and previous baselines.
Before applying the new policy, you can review and compare the policies.
Test the new version to a pilot group before converting the current policy to the new version which can get applied to the whole fleet.
Compare Policies
Select both the policies and select the Compare Baselines option and a CSV file will get downloaded

The CSV File will clearly show the rules that’s Added and what’s being Removed.
Changing Baseline Version
When you are ready to change the versions,
Select the outdated policy, Change Version option will get activated

You can select the version as below and confirm the selection. The assigned device group will get the updated policy version and if there are any new settings, they will be applied.

Conflicting Settings With Other Policies
This is very important because simply you don’t need to have the same setting set up in two different policies with different options.
Imagine you have set this ASR Rule set up in the Security Baseline policy
Block Office applications from injecting code into other processes – Block
In the Endpoint Security > Attack Surface Reduction Rules the same rule has been set to Audit
This will conflict this setting as it has 2 values in 2 policies and will end up seeing a conflict in the reports and this will not get applied to the devices.
However, if you setup Not Configured in one policy for the same setting if that option is available, the other customization will take priority over that.
Advanced Settings Available in Other Security Polices
This has a connection to the previous section. Security Baseline will activate some of the important settings of each aspect of the Windows OS. In some sections, it will only touch base a subset of settings and more advanced settings are available in the relevant specific policy. And you will see the same setting is available in that specific policy which you configured in the Security Baseline. This will end up in a conflict. Make sure you cross check the policies and set the settings to Not Configured in one policy to avoid those conflicts.
Example: Microsoft Defender Firewall Policy and the Firewall section in the Security Baseline
Default Inbound Action for Domain Profile setting Vs. Inbound Connections Blocked setting
Microsoft Defender Firewall Policy
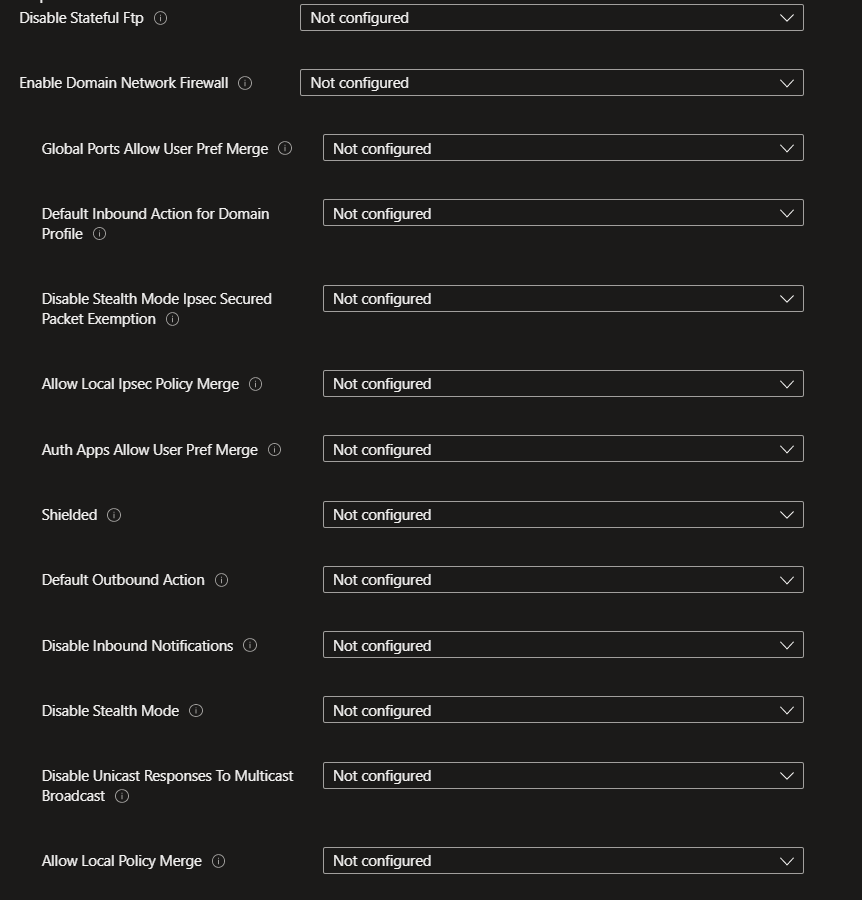
Firewall section in the Security Baseline

Removing Baseline And Settings Tattooing Issue
This is something that Microsoft has fixed, but I have seen it’s not 100%. The settings in the Security Baseline policy are a bunch of CSPs (Configuration Service Provider) that has its own setting parameters and values. The idea of removing a device group from an assignment makes those CSPs to revert back to their default value is not possible sometimes. Same as how a GPO would work. Unassuming the GPO from that user or the computer won’t remove the change that’s done most of the time.
Microsoft recommends creating a new Security Baseline and set that specific setting to Not Configured and let the device sync. But that might not work all the time if that specific setting in the Windows OS doesn’t have the Not Configured option.
This is what Microsoft has to say about it.

Reporting
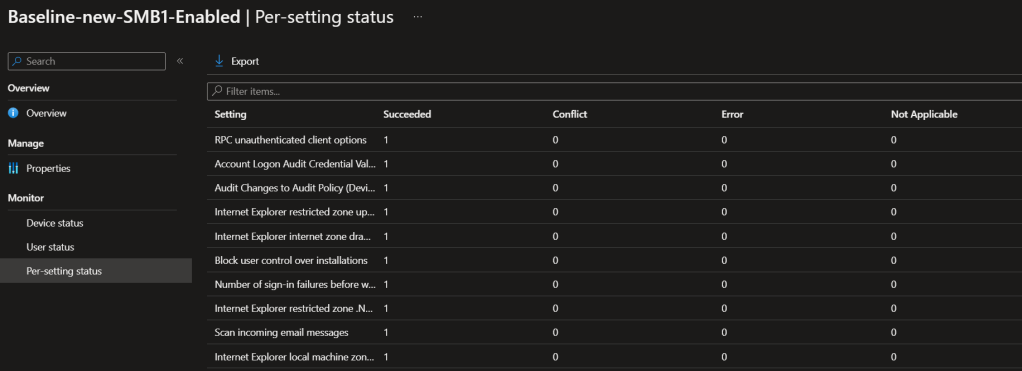
This is equally important as you need to know which devices has been synced with the policy and which settings has been ended up in error and conflict state.
Device Status

Per Setting Status
Devic Configuration reports (Select Devices > All devices > select a device > Device configuration) of device will further tell you more about the policies if they have successfully applied or will show if there are conflicting policies.
Monitor Assignment Failures and Dig Into the Settings and Devices With the Issue
Microsoft Intune Monitor section offers some good diagnostics and with a little bit of digging around you can pinpoint what’s the conflict or the error setting so you can go and change it accordingly.


Filer for Status == Conflict

Click on the Setting name and then you’ll find other profiles with the same setting

Error Handling
Event Viewer Logs are in Event viewer > Applications and Services Logs > Microsoft > Windows > DeviceManagement-Enterprise-Diagnostics-Provider > Admin location for further policy troubleshooting.
Wrapping Up
Do you need a Security Baseline? Yes. Will this be enough to protect your devices? No. Why? Microsoft have heaps of other Security policies specific to different areas of the device (BitLocker, Device Control, Firewall, ASR etc.) and they must be rolled out properly after evaluating the impact and with proper change management processes. But yes, surely the Baseline Security policies will harden your end user Windows devices as the step one of the device protection journey where you then apply the specific polices on top of it.
Discover more from EMS Route
Subscribe to get the latest posts to your email.

2 thoughts on “Device Hardening with Intune Security Baseline for Windows Policy”