To start hunting for threats and act on alerts, first the devices in the organisation must be onboarded to MDE. There are few onboarding methods that suites the organisation and I will be showcasing the steps of the commonly used setups. I will be focusing on Windows 10 devices in this article.
And finally the steps to verify the onboarding process by running a PowerShell command on on of the devices will be shown as well.
As mentioned, there are few ways of Onboarding the devices. Lets look at them now
Table of Content
- Local Script
- Group Policy
- Microsoft Endpoint Config Manager Current Branch
- Prerequisite – Tenant Attach to be enabled
- Onboard Devices via Microsoft Endpoint Manager/ Intune
- Method 1 – Set the Microsoft Defender for Endpoint and Intune connection
- How to establish the connection?
- Method 2 – Create the Onboarding Policy
- Once Onboarded Check MDE
- Final Words
Path to Onboard devices section is from https://security.microsoft.com > Settings > Endpoints > Under Device Management > Onboarding
Local Script
This method can be used for 1-10 devices as the script has been optimised for limited number of devices.
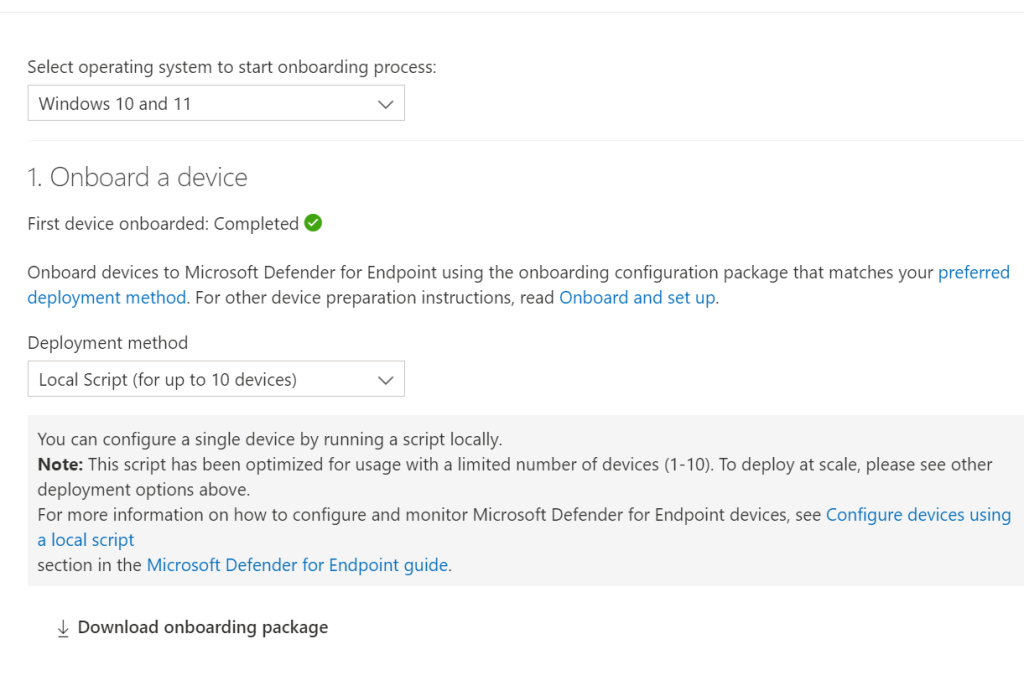
Once you download the package, then you can install it to the individual device.
Group Policy
Select Group Policy as the deployment method > Download the Onboarding package and then you can add it as a logon script (example) to onboard the devices

Microsoft Endpoint Config Manager Current Branch
Prerequisite – Tenant Attach to be enabled
Download the Onboarding Package from MDE
Go to https://security.microsoft.com > Settings > Endpoints > Under Device Management > Onboarding
Select the OS option as Windows 10 and 11
From the Deployment Method option select Microsoft Endpoint Configuration Manager Current Branch and Later

Click on Download onboarding package and save it in your device
Go to the Microsoft Endpoint Configuration Manager console
Go to Assets and Compliance > Endpoint Protection > Microsoft Defender for Endpoint Policies

Complete the Name and Description and the Policy type as Onboarding

Browse and Upload the previously downloaded onboarding package from MDE

This can be as default or according to your choice

Complete the policy creation

Once you completed creating the policy creation, you need to deploy it to a device collection
Make sure you have your device collection ready to go. In my case, the device collection name is Co-management eligible devices
Right-click on the created policy and select Deploy

Select the Device Collection as below and press OK

This will now be shown as deployed
Onboard Devices via Microsoft Endpoint Manager/ Intune
Prerequisite – Device MUST be enrolled to Intune and joined via AAD Joined or Hybrid AAD Joined Method
Method 1 – Set the Microsoft Defender for Endpoint and Intune connection
This is the easiest way as once the connection is enabled between Defender for Endpoint and Intune, the onboarding and offboarding packages are sent to the Intune and the devices which are in Intune can be onboarded to defender automatically.
According to Microsoft – The preceding screen capture shows your configuration options after you’ve configured a connection between Intune and Microsoft Defender for Endpoint. When connected, the details for the onboarding and offboarding blobs are automatically generated and transferred to Intune.
How to establish the connection?
In MEM (https://endpoint.microsoft.com > Tenant Administration > Connectors and Tokens > Microsoft Defender for Endpoint
Connection Status should be Enabled and the option Allow Microsoft Defender for Enforce Endpoint Security Configuration to ON

When you set this option to On, all devices in the platform scope in Microsoft Defender for Endpoint that aren’t managed by Microsoft Endpoint Manager will qualify to onboard to Microsoft Defender for Endpoint.

Method 2 – Create the Onboarding Policy
If you are unable to setup the connection as mentioned in the Method 1, you can use this method below.
However you will get an option Microsoft Defender for Endpoint client configuration package type displays with options to specify onboarding and offboarding blobs
In the MEM > Devices > Configuration Profiles > Create Profile
Platform: Windows 10 and later
Policy Type: Templates
Template name: Microsoft Defender for Endpoint

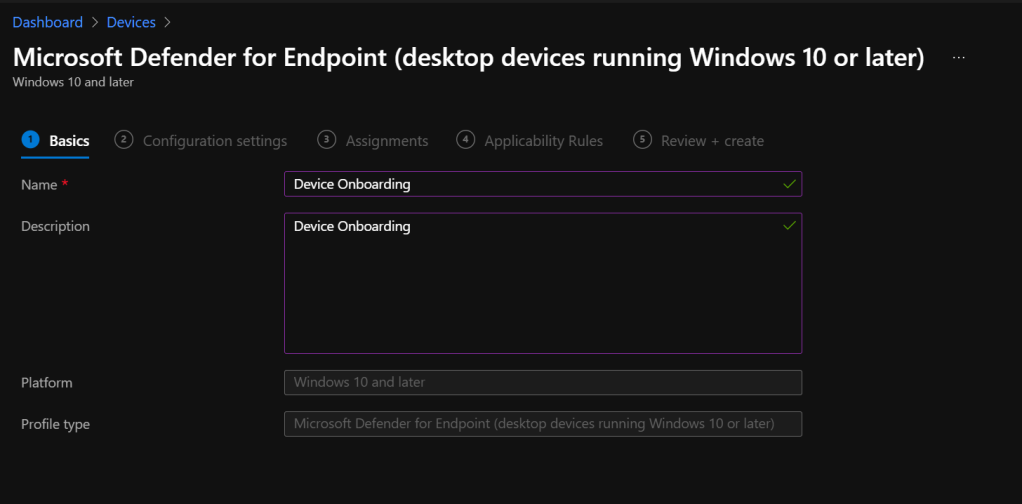

Select the Device Group. In this Example, I’ve selected the Azure AD Group Windows 10 Devices

Leave the next screen or create an Applicability Rule. This can be used if you need the assignment to be more targeted in the device group selected above


Review and Create
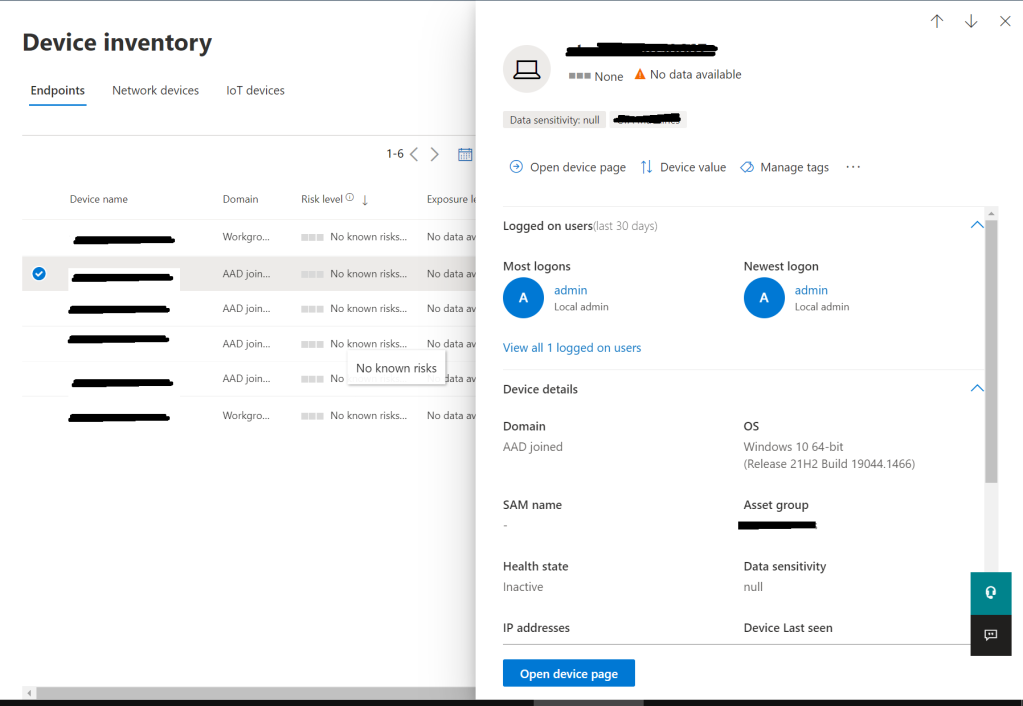
Once Onboarded Check MDE
Go to the Defender Portal > Device Inventory (under Endpoints) and you can see the Onboarded devices

And more information if you click on the device
Run a Detection Test
Now that the devices are onboarded, you need to run a detection test to verify if the onboarding happened as expected.
Run this in PowerShell on on device and you will see the result
powershell.exe -NoExit -ExecutionPolicy Bypass -WindowStyle Hidden $ErrorActionPreference= ‘silentlycontinue’;(New-Object System.Net.WebClient).DownloadFile(‘http://127.0.0.1/1.exe’, ‘C:\test-WDATP-test\invoice.exe’);Start-Process ‘C:\test-WDATP-test\invoice.exe’
Final Words
As you can see, there are few ways to onboard a device and the end result is elegant.
Why elegant? Because they will start showing in MDE for you to start monitoring, threat hunting, investigating issues and be on top of Endpoint Security.
Discover more from EMS Route
Subscribe to get the latest posts to your email.
