Continues Access Evaluation or CAE is still in preview, but it has proven to refresh the near-real time refresh for Conditional Access Policies.
Ideally this is a very helpful feature in the world of Identity and Access Management, because there are frequent attacks happening and the IdAM Admins need to take action quickly.
Some actions including Reset user password, adding or removing Trusted IPs and specially when the user is moving from location to location and when the Conditional Access policies to govern the trusted locations.
Usually the token expiration and refresh interval is 1 hour and ideally when a client application that is Modern Authentication aware tries to connect, the API requests are authorized using OAuth 2.0 access tokens.
Every hour, when they are due to refresh, it reevaluates the user state, policies in order to enforce what’s in the policy.
The client app redirects back to the Azure AD to refresh the token and according to the user state, the new token will make sure whether the user access to be blocked or to be allowed.
Key Benefits of enabling CAE
- User termination or password change/ reset: User session revocation will be enforced in near real time
- Network location change: Conditional Access location policies will be enforced in near real time
- Token export to a machine outside of a trusted network can be prevented with Conditional Access location policies
Azure AD Sync Should happen 1st
Although the token refresh is near-real time, In a Hybrid environment, the time to replicate the user state to Azure AD will take 30 mins unless you have specified a shorter interval or if you changed the user state in between the interval.
Currently the CAE is in used for Exchange Online, Microsoft Teams and SharePoint Online
If your app needs to have CAE aware APIs, there is a special configuration that needs to be done which can be found here How to use Continuous Access Evaluation enabled APIs in your applications – Microsoft identity platform | Microsoft Docs.
What will be evaluated?
- User Account is deleted or disabled
- Password for a user is changed or reset
- Multi-factor authentication is enabled for the user
- Administrator explicitly revokes all refresh tokens for a user
- High user risk detected by Azure AD Identity Protection
What is Claim Challenge?
In a world where CAE is not introduced, the client can replay the token the cache until it expires.
With CAE, the resource provider can reject the token even when the token is not expired.
With Claim- Challenge, it will reject the current token and a new token will be issued by Azure AD.
This to work, the apps should have the latest version installed as well.

A user revocation event flow
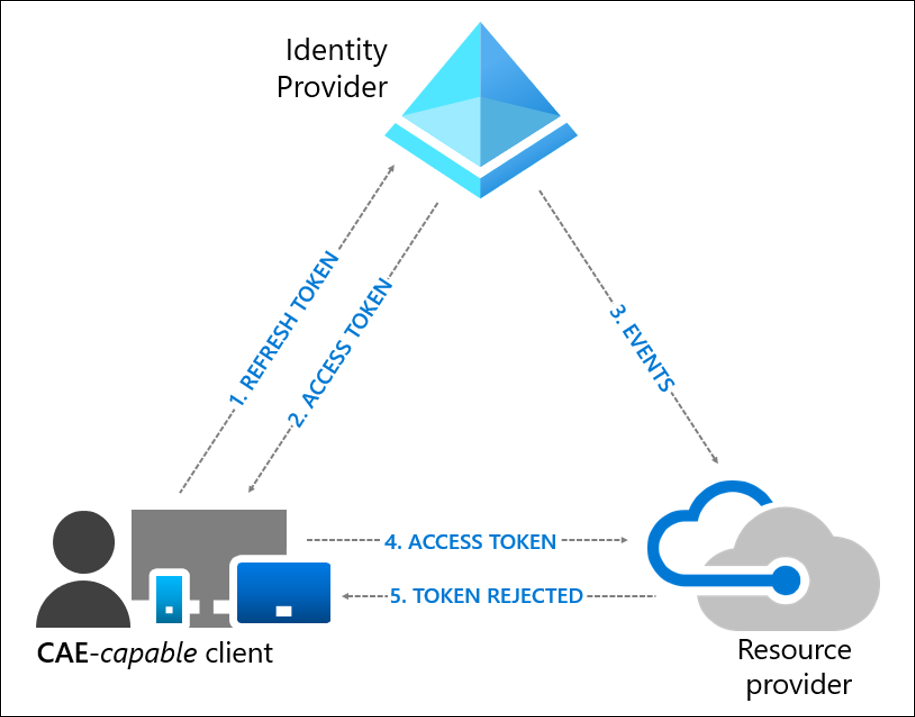
- A CAE-capable client presents credentials or a refresh token to Azure AD asking for an access token for some resource.
- An access token is returned along with other artifacts to the client.
- An Administrator explicitly revokes all refresh tokens for the user. A revocation event will be sent to the resource provider from Azure AD.
- An access token is presented to the resource provider. The resource provider evaluates the validity of the token and checks whether there is any revocation event for the user. The resource provider uses this information to decide to grant access to the resource or not.
- In this case, the resource provider denies access, and sends a 401+ claim challenge back to the client.
- The CAE-capable client understands the 401+ claim challenge. It bypasses the caches and goes back to step 1, sending its refresh token along with the claim challenge back to Azure AD. Azure AD will then reevaluate all the conditions and prompt the user to reauthenticate in this case.
Conditional Access Policy to enforce access restrictions based on location
In a situation like this,
- When the user tries logs in to the application from a location, Azure AD evaluates all Conditional Access Policies to see whether the user and client meet the conditions.
- If all good, an access token will be issued by Azure AD and login flow will be completed
- Given the fact that user moves out of an allowed IP range, the client will present an access token to the resource provider from outside of n allowed IP range
- Resource provider evaluates the validity of the token and and checks the location policy (Conditional Access Policy) synced from Azure AD.
- If the user moved in to a restricted IP range, the resource provide denies access and sends a 401 + claim change back to the client because the request if not coming from a allowed IP range
- CAE-aware client understands the 401 + claim change and it bypass the cache (Claim Challenge) and refreshed the token and Azure AD reevaluates all the conditions and will deny access in this case
How to enable CAE?
Login to the AAD Portal > Security > Security | Continuous access evaluation (Preview)
Select Enable
Select the users (All users and groups or Selected users and groups)

Worth Mentioning
- Sign-in frequency in the Conditional Access Policy will be honored with or without CAE
- If you enable a user right after it is disabled. There will be some latency before the account can be enabled. SPO and Teams will have 15-mins delay. The delay is 35-40 minutes for EXO.
- Group updated and policy changes will take about one day to be effective. In an urgent situation, you can either revoke user session from the user’s AAD profile from Azure AD > Users > Select the user > Authentication Methods
Or run the below PowerShell command
Revoke-AzureADUserAllRefreshToken -ObjectId “<object_id>” - In a situation where few users are on an file (Co-Authoring) and when the CAE applied, the user will not lose access the same time. For this to happen, it will take around 10 hours or after closing the file
- TO reduce this time, SPO admins can change the maximum lifetime of co-authoring sessions. And the maximum can be reduced to 15 minutes. This command can achieve that in the tenant Set-SPOTenant –IPAddressWACTokenLifetime
Discover more from EMS Route
Subscribe to get the latest posts to your email.

One thought on “Why Azure AD Continues Access Evaluation is Important?”